Key Highlights:
- A significant provide chain assault compromised npm packages resembling “debug” and “chalk” which might be broadly utilized by JavaScript and EthereumJS initiatives.
- Attackers injected malicious code that silently swapped cryptocurrency addresses throughout transactions.
- The assault failed resulting from coding errors.
An enormous provide chain assault concentrating on the broadly used JavaScript package deal “debug” (a instrument that builders use to log data and troubleshooting apps), was revealed in the present day, September 9, 2025. On this hack, as an alternative of attacking any of the person initiatives, hackers managed to compromise this instrument which permits malicious code to unfold wherever it was put in. Since Ethereum JS libraries and a number of different initiatives primarily depend on “debug,” the chance of knowledge theft or deep breaches was important.
The assault was disclosed on the undertaking’s GitHub problem tracker, the place maintainers confirmed that attackers had gained entry to publishing credentials. Ledger’s CTO, Charles Guillemet, had posted about this menace yesterday on X and tried to warn customers. Nonetheless, the CTO has now confirmed that the replace was rapidly detected and the variety of victims was minimal as a result of the flawed code induced crashes in CI/CD pipelines, elevating pink flags early on.
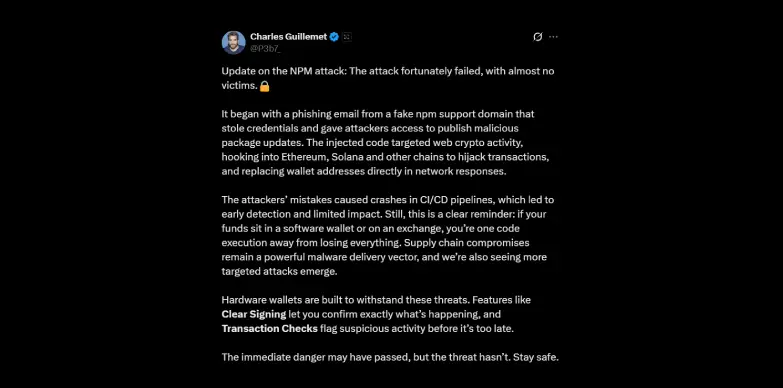
What Occurred?
On September 9, 2025, it has been revealed by the safety consultants that hackers managed to interrupt into the NPM account of a trusted developer (Josh Junon) and pushed out a pretend replace (v4.4.2) of the favored “debug” package deal. This instrument or package deal is used within the JavaScript world and EthereumJS libraries slightly an excessive amount of, with over 2 billion weekly downloads, so the assault had the capability to unfold to many apps and methods.
The malicious code had been designed right here in such a approach that it may secretly swap out actual cryptocurrency pockets addresses with the attacker’s personal, stealing funds with out the customers noticing. Since many of the corporations that use open-source instruments like “debug” with out questioning them, a single poisoned replace may have unfold like a wildfire. However in observe, the attackers’ implementation errors induced failure that made detection far simpler. This led to restricted unfold and prevented widespread theft.
How Did the Assault Work?
As talked about above, the attackers compromised developer’s NPM credentials and pushed a malicious replace of the “debug’ package deal. What the developer didn’t know was, there was a hidden operate that secretly changed respectable crypto pockets addresses with those managed by the hackers. Every time apps utilizing this package deal generated blockchain transactions, the funds had been redirected with out the customers ever noticing, however as a result of the replace crashed pipelines, the try backfired and was stopped early.
Might It Get Worse?
Regardless that this assault failed, it exhibits how dangerous the state of affairs would have been if the CI/CD pipelines had not crashed. Poisoned updates may have acted like Trojan horses and they might have embedded themselves into varied initiatives. If this assault was executed with extra precision, it will have affected monetary apps, exchanges and even non-crypto platforms that rely upon the identical instruments.
Ledger CTO had emphasised on this X publish, customers of {hardware} wallets with clear transaction signing stay protected, as they’ll confirm particulars earlier than signing and stop silent handle swaps.
Precautions to Take Instantly
- Just be sure you run npm ls debug in your undertaking’s listing and in the event you occur to see model 4.4.2 put in, take away it instantly and do a clear reinstall from a trusted supply.
- In case you are not utilizing a {hardware} pockets with clear transaction signing, strive to not perform any blockchain transactions till this menace is totally mitigated.
- {Hardware} wallets as talked about by Ledger CTO present a security layer which requires guide approval of transaction particulars so one can simply spot unauthorized handle modifications.
- Make it possible for your confirm the recipient handle on transaction affirmation screens earlier than signing.
- Comply with official repos, npm advisories and dependable safety channels for updates on the incident.
Additionally Learn: OpenLedger (OPEN) Surged 200% Right now- Right here’s Why the Rally Ignited
Key Highlights:
- A significant provide chain assault compromised npm packages resembling “debug” and “chalk” which might be broadly utilized by JavaScript and EthereumJS initiatives.
- Attackers injected malicious code that silently swapped cryptocurrency addresses throughout transactions.
- The assault failed resulting from coding errors.
An enormous provide chain assault concentrating on the broadly used JavaScript package deal “debug” (a instrument that builders use to log data and troubleshooting apps), was revealed in the present day, September 9, 2025. On this hack, as an alternative of attacking any of the person initiatives, hackers managed to compromise this instrument which permits malicious code to unfold wherever it was put in. Since Ethereum JS libraries and a number of different initiatives primarily depend on “debug,” the chance of knowledge theft or deep breaches was important.
The assault was disclosed on the undertaking’s GitHub problem tracker, the place maintainers confirmed that attackers had gained entry to publishing credentials. Ledger’s CTO, Charles Guillemet, had posted about this menace yesterday on X and tried to warn customers. Nonetheless, the CTO has now confirmed that the replace was rapidly detected and the variety of victims was minimal as a result of the flawed code induced crashes in CI/CD pipelines, elevating pink flags early on.

What Occurred?
On September 9, 2025, it has been revealed by the safety consultants that hackers managed to interrupt into the NPM account of a trusted developer (Josh Junon) and pushed out a pretend replace (v4.4.2) of the favored “debug” package deal. This instrument or package deal is used within the JavaScript world and EthereumJS libraries slightly an excessive amount of, with over 2 billion weekly downloads, so the assault had the capability to unfold to many apps and methods.
The malicious code had been designed right here in such a approach that it may secretly swap out actual cryptocurrency pockets addresses with the attacker’s personal, stealing funds with out the customers noticing. Since many of the corporations that use open-source instruments like “debug” with out questioning them, a single poisoned replace may have unfold like a wildfire. However in observe, the attackers’ implementation errors induced failure that made detection far simpler. This led to restricted unfold and prevented widespread theft.
How Did the Assault Work?
As talked about above, the attackers compromised developer’s NPM credentials and pushed a malicious replace of the “debug’ package deal. What the developer didn’t know was, there was a hidden operate that secretly changed respectable crypto pockets addresses with those managed by the hackers. Every time apps utilizing this package deal generated blockchain transactions, the funds had been redirected with out the customers ever noticing, however as a result of the replace crashed pipelines, the try backfired and was stopped early.
Might It Get Worse?
Regardless that this assault failed, it exhibits how dangerous the state of affairs would have been if the CI/CD pipelines had not crashed. Poisoned updates may have acted like Trojan horses and they might have embedded themselves into varied initiatives. If this assault was executed with extra precision, it will have affected monetary apps, exchanges and even non-crypto platforms that rely upon the identical instruments.
Ledger CTO had emphasised on this X publish, customers of {hardware} wallets with clear transaction signing stay protected, as they’ll confirm particulars earlier than signing and stop silent handle swaps.
Precautions to Take Instantly
- Just be sure you run npm ls debug in your undertaking’s listing and in the event you occur to see model 4.4.2 put in, take away it instantly and do a clear reinstall from a trusted supply.
- In case you are not utilizing a {hardware} pockets with clear transaction signing, strive to not perform any blockchain transactions till this menace is totally mitigated.
- {Hardware} wallets as talked about by Ledger CTO present a security layer which requires guide approval of transaction particulars so one can simply spot unauthorized handle modifications.
- Make it possible for your confirm the recipient handle on transaction affirmation screens earlier than signing.
- Comply with official repos, npm advisories and dependable safety channels for updates on the incident.
Additionally Learn: OpenLedger (OPEN) Surged 200% Right now- Right here’s Why the Rally Ignited





















